Example OpenID Connect (OIDC) Setup: Keycloak
On this page we describe how to set up Keycloak as an OpenID Connect (OIDC) provider for Klutch. Please see Keycloak's documentation to learn how to deploy Keycloak.
OpenID Connect (OIDC) client for the backend
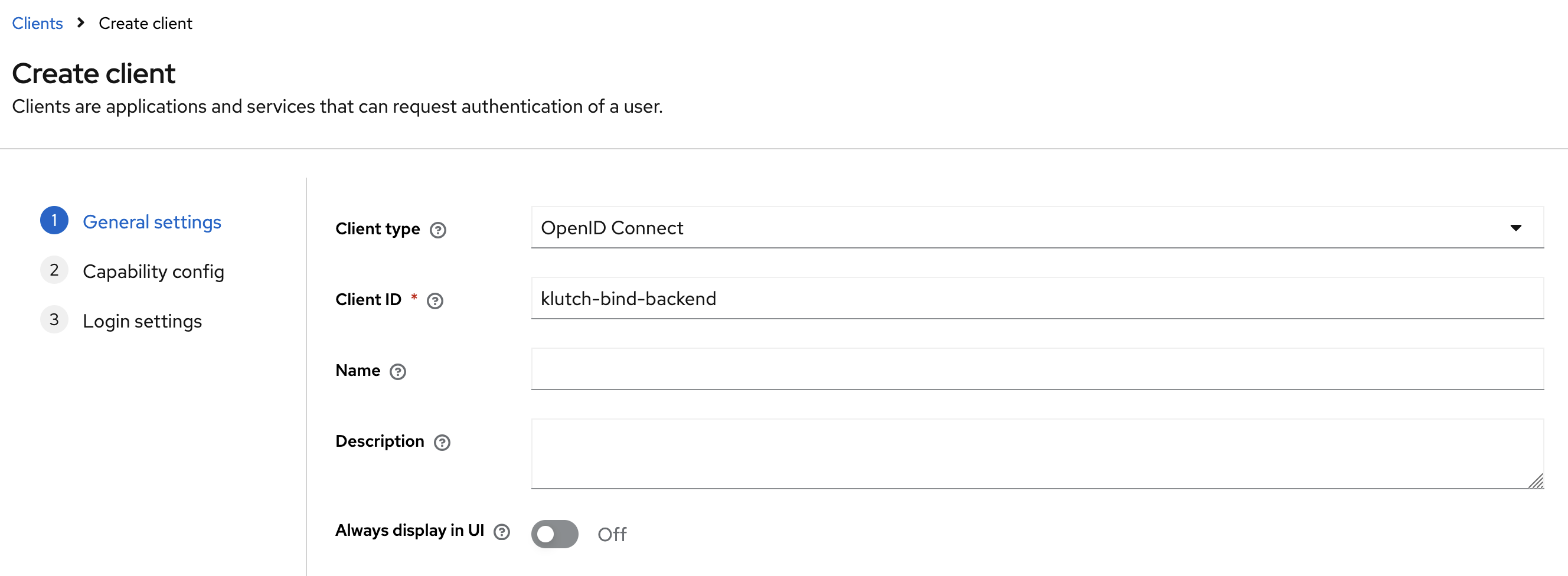
The Klutch backend needs to be configured as an OIDC client so that developers can authenticate
against it and set up service accounts for App Clusters
to connect (bind) to data services. For this purpose, create a new OIDC client for the Klutch
backend. In our example we call the client klutch-bind-backend.
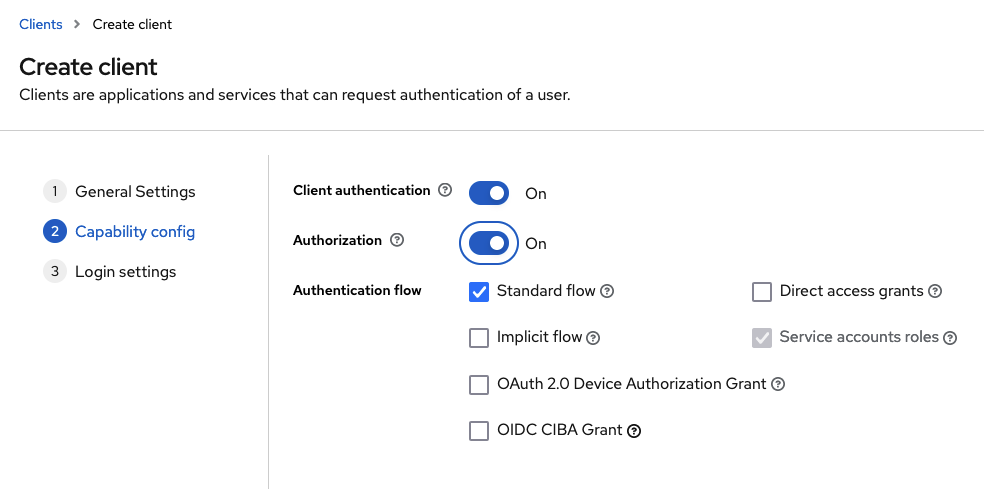
Enable Client authentication and Authorization, so that Keycloak users can authenticate against the backend. Select all the flows you want to enable. For the web based setup Standard Flow is required.
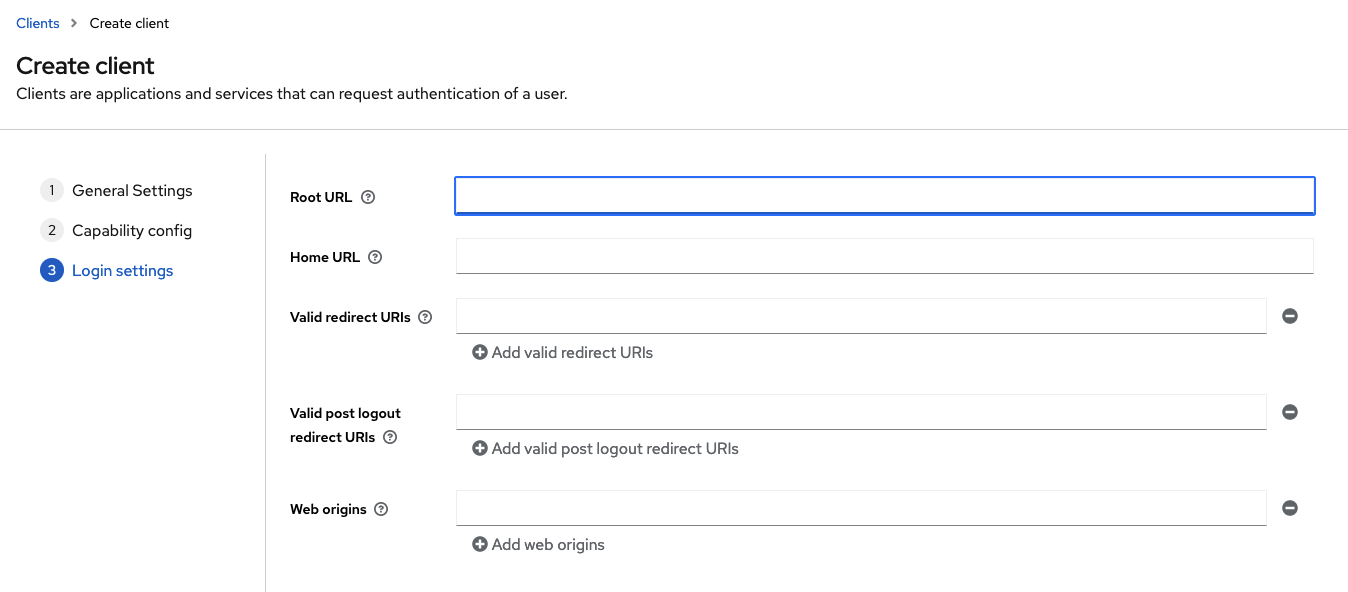
Set up Root and Home URLs as required. For Valid redirect URLs please add
<BACKEND_URL>/callback. Replacing <BACKEND_URL> with the base URL of the Klutch backend.
OIDC setting for Users
Currently no special setup is required for users. All users in keycloak can create a binding.